On Entropy and Passphrases
Passphrases have been in the news again lately, because of a big data breach at Lastpass, which may have been more serious than Lastpass first revealed.
That got me thinking: how secure is a passphrase vs. a random password?
Passwords
I assume you use random passwords generated by a password manager like Lastpass, Dashlane, 1Password, or Bitwarden (which I use). If you have it set up to create 12 or more characters with upper and lower case, digits, and punctuation, those passwords should be very secure.
If you create your own memorable passwords, they are certain to be less random, and thus more guessable. For instance many attackers start with lists of common English words (and permutations thereof), and known common passwords. There are many fewer possibilities than if you use a random password, so it’s not recommended. The downsides are you can’t remember random ones, they’re hard to type, and even harder to type on a small screen.
Entropy
The standard measure of how hard a password is to crack is entropy, measured in bits. A single coin has one bit of entropy: it can be up or down. A six-sided die has about 2.5 bits of entropy: . As long as an attacker doesn’t have any special info, the entropy is directly related to how long it would take them to guess by “brute force” – checking all possibilities. Each additional bit doubles the amount of time it would take to guess.
A random password composed of 26 lowercase characters, 26 uppercase, 12 punctuation, and ten digits gives bits per character, or a total of 74 bits for a 12-digit password, or 86 bits for a 14-digit password. This is plenty for “regular people” (if you’re not a journalist, activist, wealthy, or other high profile target). If you are a high-value target, you need at least 128 bits of entropy, or about 20 random characters. It doesn’t hurt to use a password that long for your most important accounts, such as your bank. Just hope you never have to type it in.
But what about passphrases?
Passphrases
The best practice for passphrases is to use a few words mashed together, sometimes with spaces and/or digits intermixed. The XKCD “correct horse battery staple” one is a famous example.
But how good are they really?
A passphrase is certainly longer than a 14-digit random password. So if the attacker doesn’t know how you came up with it, and they have to try all possible combinations of random passwords up to the 28-character length of “correct horse battery staple”, the entropy is huge: bits!
But if passphrases become popular, attackers will try them first, rather than trying everything willy-nilly. In cryptography, it’s always safest to assume the adversary is as smart as possible.
A common word list used by passphrase generators is diceware; that list has 7776 words. (It’s called diceware because you can generate words from it by rolling dice using a simple process.) That gives about 12.9 bits of entropy per word, or a bit more if you capitalize randomly or stick a digit or punctuation in here or there.
In this case, a four-word passphrase has only 51 bits of entropy, and a five-word phrase has 64. A six-word phrase has 77 bits, a bit better than a 12-digit random password.
Six words is a lot to type, for sure, but it’s certainly easier to
type “city linguini muster hatbox juiciness caretaker” than
9xpzw%T5q^oh. You can also tell it to someone over the phone (good
luck even knowing i from l and 0 from O in random passwords).
But for me the biggest advantage is for TV streaming services, where I
sometimes have to type the passphrase into those horrible
hunt-and-peck keyboards on the TV.
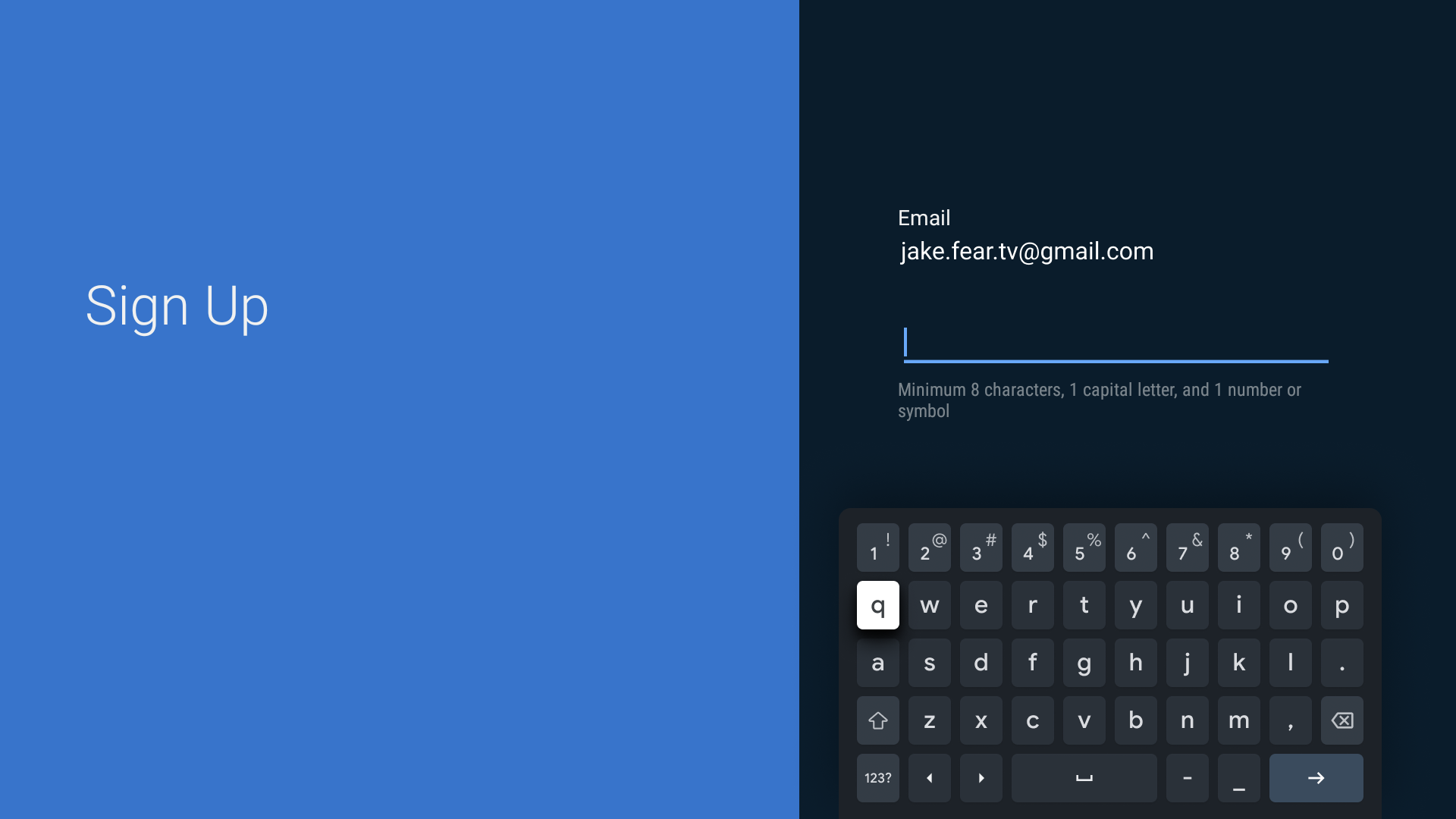
For these, a set of nice lowercase words is so much easier. And if you use five or six diceware words, it’s as secure as a random password. Bitwarden, the password manager I use, will generate diceware passphrases for you, so it’s no more work.
So… Should I Switch?
I thought about switching to passphrases for many online accounts, but after thinking it through, I plan to stick with random passwords for most, and use passphrases only when memorability or typeability matter.
I suggest using a long randomly generated passphrase as your master password for your password manager, with a few digits and punctuation chars mixed in. You will have to type that fairly regularly, and it is your highest value target (since it unlocks everything else), so, to state the obvious, don’t use your mother’s maiden name or your birthday for it. Choose wisely.
Two Factor Auth
No matter what kind of password or phrase you use with your online accounts, you should always enable “2FA” or two-factor authentication. Whether it’s SMS to your phone, an authenticator app, or a physical security key, anything is better than nothing: don’t forget that “brute force” password cracking is the last resort of the bad guys. Social engineering, looking over your shoulder, malware, or sniffing unencrypted network traffic are all ways passwords can become exposed. If you have 2FA enabled, those passwords become a lot less useful. So be safe out there!

